Today, the Internet is a tool for espionage, part of which is the analysis of users’ personal data. The American creative agency We Are Social stated that at the beginning of 2022, almost 62.5% of the world’s population uses the Internet – the number of users in 2021 increased by 192 million (4%) and is 4.95 billion people. Providers collect gigabytes of information about their clients every day – frequently visited places, hobbies, search queries, even food preferences – that is, all the information that people leave online. We should not forget that such large companies as Microsoft, Google, Apple, VK and Yandex Inc., which are actively developing and popularizing cloud storage technologies, cooperate with intelligence agencies. Given this fact, users should seriously think about how to protect their privacy from prying eyes. Each new round of development of information technology leads to an increasing compromise of all users. That is why ensuring anonymous work in public information networks is one of the most important issues of our time.
1.1 Anonymity when working online
Anonymity is a concept related to untraceability. It expresses the opportunity granted to participants (of a protocol) to perform some action anonymously, i.e. without identifying themselves. However, the participant is obliged to prove their right to perform this action. Anonymity can be absolute or revocable. In the latter case, the system has a dedicated participant, an arbitrator, who, under certain conditions, can violate anonymity and identify the participant who performed this specific action [Dictionary of Cryptographic Terms / Ed. by B.A. Pogorelov and V.N. Sachkov. – M.: MCNO, 2006.– 94 p.].
Anonymity on the Internet implies the absence of a connection between a real person and an Internet user. Due to progress in information technology, it is becoming increasingly difficult to hide this connection every year. All user data that remains on the Internet, the so-called digital footprint, is collected, analyzed and used, for example, by law enforcement agencies to search for information about suspects. However, they can be used by intruders in such illegal actions as collecting, storing, using and distributing information about a person’s private life without their consent and illegally revealing the secret of correspondence, telephone conversations, postal, telegraph and other messages.
Currently, there are two directions for anonymizing work on the Internet: organizational and software and hardware.
The organizational method involves creating a “new” virtual personality or using an existing one, on behalf of which the user will carry out his/her activities. An example of the implementation of this method is the use of a fake page on a social network. The main difficulty in achieving a positive result when using this method is that the user must have serious skills in the field of social engineering.
The software and hardware direction is in turn subdivided into software and hardware anonymization methods. The hardware method includes the use of third-party technical means not associated with the user to achieve their goals. A significant disadvantage of this method is the user’s dependence on other people’s resources and, consequently, the lack of constant access to them.
The most effective way to organize anonymous work on the Internet is to use special security services – anonymizers. Anonymizers are designed to meet the functional requirements of privacy – class FPR of the “General Criteria” (GOST R ISO/IEC 15408-2008). The FPR class contains four families: FPR_ANO (anonymity – the ability to perform actions without disclosing the identification data of users), FPR_PSE (pseudo-anonymity – anonymity with preservation of accountability), FPR_UNL (impossibility of association – anonymity with concealment of the connection between the actions of one user), FPR_UNO (concealment or unobservability – concealment of the very fact of using a resource or service). The most widely used are VPN and TOR.
1.2 Virtual Private Network
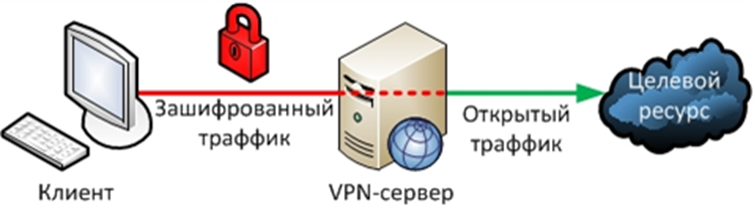
VPN is a technology that allows you to implement such operations as hiding the user’s IP address for anonymous use of the Internet and overcoming regional censorship to gain access to Internet resources prohibited in the user’s region.
When using a VPN, the connection to the Internet is not made directly through the provider, but through a connection to a VPN server. A closed communication channel is created between the user and this server, the contents of which cannot be seen even by the user’s Internet provider, since the data transmission channel is encrypted. The VPN server acts as an Internet access provider, and all that the user’s provider sees is that encrypted traffic is being sent between the user and the server.
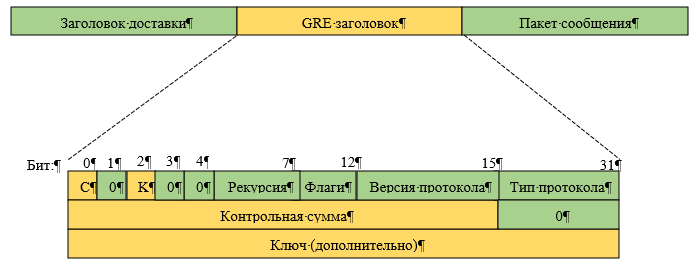
To explain how VPN works, we must first understand what happens to an IP packet when it passes through a VPN server. To do this, let’s look at the operation of the protocol that encapsulates network layer protocol packets – GRE.
Let’s assume that we have two networks A and B, between which a VPN server is located. If a host from network A wants to access an FTP server in network B, then the host in network A will send a packet in which the destination address will be the IP address of the FTP server, and the source address will be its own.
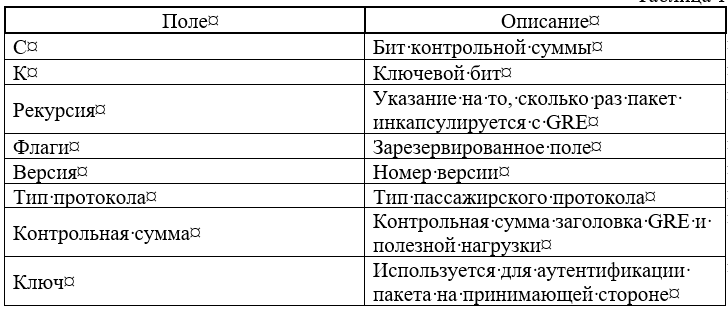
When the original packet reaches the incoming VPN gateway, it will be processed by the GRE protocol, that is, the packet will be encapsulated, for example, in an IP packet with a GRE header.
After encapsulation, the original packet is encrypted (usually AES) and a “new” plaintext IP header is added (the “new” header is moved across the Internet) where the destination address is the exit VPN gateway and the source address is its own. It must be open for error-free routing. For this, a new checksum is also calculated (since the original is encrypted). The new checksum of the “new” packet must be calculated when it appears, otherwise it will not be able to move across the Internet (for example, PPP is sometimes used between nodes on the Internet where the checksum is calculated). Therefore, there must be two checksums in the entire packet.
The packet can then travel across the Internet to the exit VPN gateway. Here, the original header or the packet type itself will not matter, as the packet will be encapsulated with an IP header to travel across the Internet and other routers will not care about the original header, as they will only see the “new” IP header.
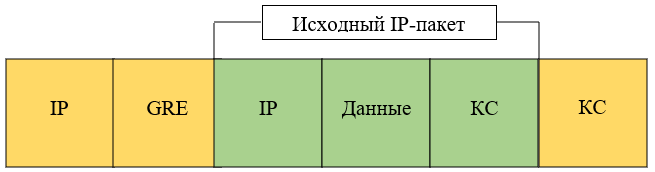
Finally, when the packet reaches the egress VPN gateway, the “new” IP header is removed and the packet is processed by the GRE protocol, which removes the GRE header and sends the original packet to network B (the FTP server).
Thus, VPN is a set of technologies that allow you to create a logical network over a physical one. It is used to ensure protection of traffic from interception by intruders and safe activity on the Internet. VPN opens access to blocked resources. However, using VPN has significant disadvantages. For example, when connecting to a VPN server, our Internet speed and bandwidth will directly depend on the location and capabilities of the server. Another disadvantage is that most “bad” users use the most popular VPN services. Therefore, if such a user does something illegal using the IP address provided to him (for example, violates the rules of communication on the forum), then this IP address will be blocked by the server of this forum. Then the “good” user, upon receiving a blocked IP address, will not be able to access the forum.
1.3 The Onion Router
Tor is an anonymization tool that passes data through several computer nodes, encrypting their addresses and the data itself, thereby providing the user with a secure data transmission channel.
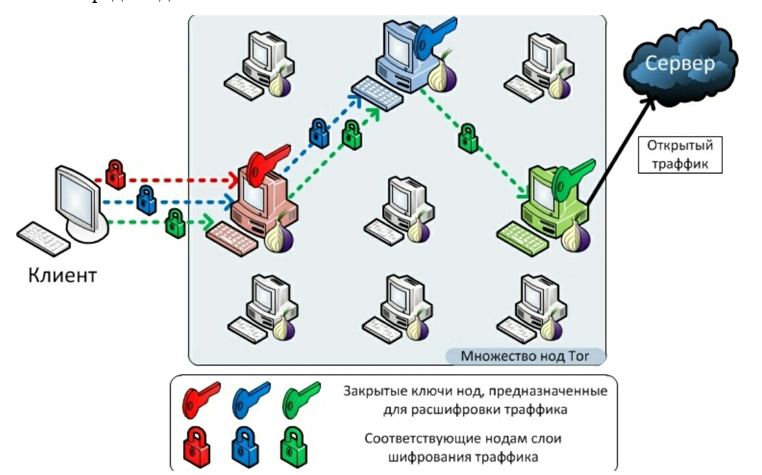
Tor uses the same communication lines as other devices on the network to connect its nodes, the same servers, the same TCP/IP protocol stack, and the same encryption algorithms to protect user data.
The Tor network consists of many computer servers, each called a Tor node, all maintained by trusted volunteers such as individuals, schools, and companies.
In this network, packets are supplemented with encrypted layers. They pass through at least three nodes: the input node, which first receives the packet from the user, an intermediate node, which prevents the output node from finding out which input node the user used, and an output node, which reveals the destination address. Each node cancels the upper layer, thereby learning the address of the next one. When the last layer is decrypted, the message reaches the recipient.
The entire message path, when working with the Tor browser, is placed in the packet header. The source address is encrypted and placed in the “Data” field so that the response from the requested server can return back to the user.
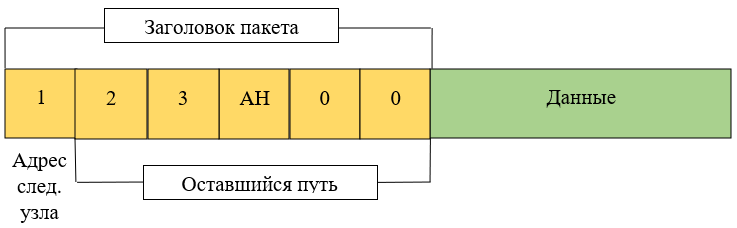
The path of the packet in the Tor network is shown in Figure 4. On the Tor browser client terminal, the packet looks like Figure 5. The “Next Node Address” window is not encrypted, unlike the “Remaining Path”. Encryption is performed on the initial node – the Tor browser user’s computer so that each node in the Tor network can determine only the address of the next node, without knowing the remaining path.
After the input node receives the packet, it decrypts the top layer and finds out the address of the next node. The packet will then look like this:
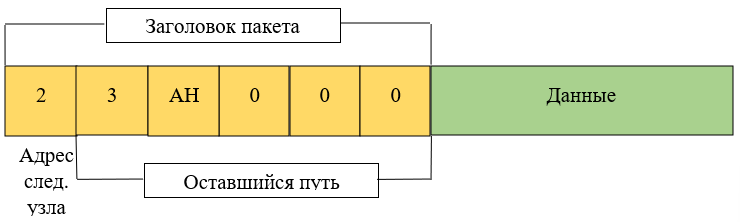
This process continues until the exit node decrypts the destination address, which is in the AH field. After this, the message reaches the addressee.
Thus, using the Tor browser allows anonymous work on the Internet by redirecting the user’s traffic through various Tor nodes. But even taking into account that the data is encrypted at each node, the end point of the connection at the exit node can be compromised if the requested site does not use an SSL connection, since there is a risk of data compromise. And just as in the case of using a VPN, the data transfer speed and throughput will depend on the physical location and capabilities of the Tor nodes used.









